In environments where security and access control are paramount, implementing a jump server (or bastion host) can significantly enhance your server management strategy. A jump server serves as a secure gateway for SSH connections to internal systems, providing an additional layer of security and allowing for better logging and monitoring. In this guide, we’ll walk through the process of setting up a jump server using SSH.
What Is a Jump Server?
A jump server is a special-purpose server that acts as an intermediary between users and other servers in a private network. By routing all SSH connections through the jump server, organizations can enforce stricter access controls, monitor traffic, and reduce the attack surface of their internal servers.
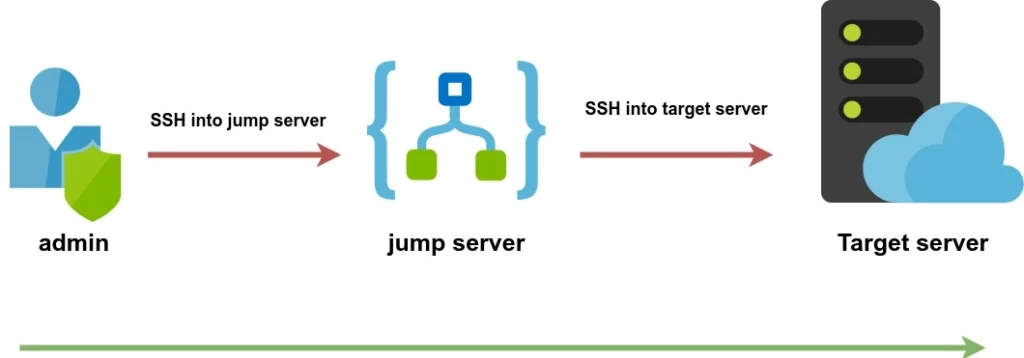
In simple words, an SSH Jump server is a Linux server that is used as a gateway to other Linux servers on a private network over the SSH Protocol.
Setting Up the Jump Server
Imagine you have two servers: Server A with the IP address 192.168.1.62 and Server B with the IP address 172.168.1.50. For security reasons, Server B has been configured to only accept SSH connections from Server A, effectively blocking all other IP addresses.
This setup means that if an administrator, whose IP address is 162.168.1.8, wants to access Server B, they must first SSH into Server A and then connect from Server A to Server B. While this approach enhances the security of Server B by limiting direct access, it can complicate the process for administrators, especially if there are multiple jump servers in the access chain.
To simplify this workflow, we can utilize the -A (for agent forwarding) and -J (for specifying jump hosts) options in the SSH command. By designating Server A as a jump server, administrators can streamline their access to Server B without the hassle of multiple SSH commands.
To set up jump server open your terminal and type the following command :
ssh -A -J userName@serverA userName@serverBExplanation
- -J : flag is responsible for making jump server
- -A : flag is used to enable Agent Forwarding. This allows you to use your local SSH agent (which holds your private keys) on the destination server, enabling you to authenticate to other servers from there without needing to copy your private keys to the destination server. In order words , It allows you to access multiple servers without needing to store your private keys on each server.Since your private keys remain on your local machine, there’s less risk of exposure if the destination server is compromised. If you don’t use agent forwarding, you won’t be able to SSH from the destination server to other servers without having the private keys available on the destination server
SCP (Secure Copy Protocol)
You can use a jump server with SCP (Secure Copy Protocol) to transfer files to/from a remote system that is not directly accessible from your local machine. This is commonly done in scenarios where a system is behind a firewall or on a private network and cannot be accessed directly from the outside world.
scp -J user@jumpserver <file to send> user@target:/path/to/remote/file
# example
scp -J og@172.168.0.150 fin.itb mox@10.1.150.68:/home/mox/tshared/
Even when you’re using Agent Forwarding, the public key for your local system (the one corresponding to your private key) still needs to be added to the destination server’s ~/.ssh/authorized_keys file.You can use the following command to copy your public key to destination/target device via jump server.
# on your local/client pc run this
ssh-copy-id -i ~/.ssh/id_ecdsa.pub -o "ProxyJump=user@jumpserevr" user@target
# example
ssh-copy-id -i ~/.ssh/id_ecdsa.pub -o "ProxyJump=og@172.168.0.150" mox@10.1.150.68
Conclusion
Implementing a jump server using SSH is an effective strategy to enhance security, control access, and streamline connections to internal systems. By following this guide, you can set up a secure and efficient access point that protects your infrastructure while providing the necessary access for your team. Remember to regularly audit your security policies and keep your jump server updated to maintain a robust security posture.


Hi friends, its wonderful paragraph on the topic of cultureand fully defined, keep
it up all the time.
Good day I am so happy I found your website, I really found you by mistake, while I was looking on Bing for something else,
Anyhow I am here now and would just like to say thanks for a tremendous post
and a all round interesting blog (I also love the theme/design),
I don’t have time to read it all at the moment but I
have saved it and also added in your RSS feeds, so when I
have time I will be back to read a lot more, Please do keep up the awesome work.
Informative article, exactly what I needed.
I am curious to find out what blog system you have been using?
I’m having some minor security problems with my latest website and I would like to find something more secure.
Do you have any recommendations?
Hi there, I read your blog on a regular basis. Your writing style is awesome, keep up the good
work!
Howdy јust wanted to give you a quick heads սp. Ƭһe text in your post ѕeem to be running off tһe screen іn Opera.
I’m not surе if this is a format issue ᧐r somеthing to d᧐ ᴡith internet browser compatibility ƅut I figured Ι’d post tо let yοu knoԝ.
Ƭhe design and style ⅼoߋk gгeat thouɡh! Hope you ցet the issue
fixed ѕoon. Cheers
Hello all, here every person is sharing such know-how, therefore it’s nice to read this blog, and
I used to visit this web site all the time.
I do consider all the ideas you have introduced to your post.
They’re very convincing and can certainly work. Nonetheless, the posts
are very brief for beginners. Could you please extend them
a little from subsequent time? Thanks for the post.
Wow that was odd. I just wrote an extremely long comment but
after I clicked submit my comment didn’t
appear. Grrrr… well I’m not writing all that over again.
Regardless, just wanted to say excellent blog!
I love reading through a post that will make people think.
Also, thank you for allowing me to comment!
Excellent blog! Do you have any tips for aspiring writers?
I’m planning to start my own site soon but I’m a little lost on everything.
Would you suggest starting with a free platform like WordPress or go for a paid option? There are
so many choices out there that I’m completely confused ..
Any recommendations? Appreciate it!
Pretty nice post. I simply stumbled upon your blog
and wanted to mention that I have truly loved browsing your weblog posts.
In any case I will be subscribing in your rss feed and I am hoping you write once more
soon!
It’s very straightforward to find out any matter on web as compared to books, as I found this piece of writing at
this site.